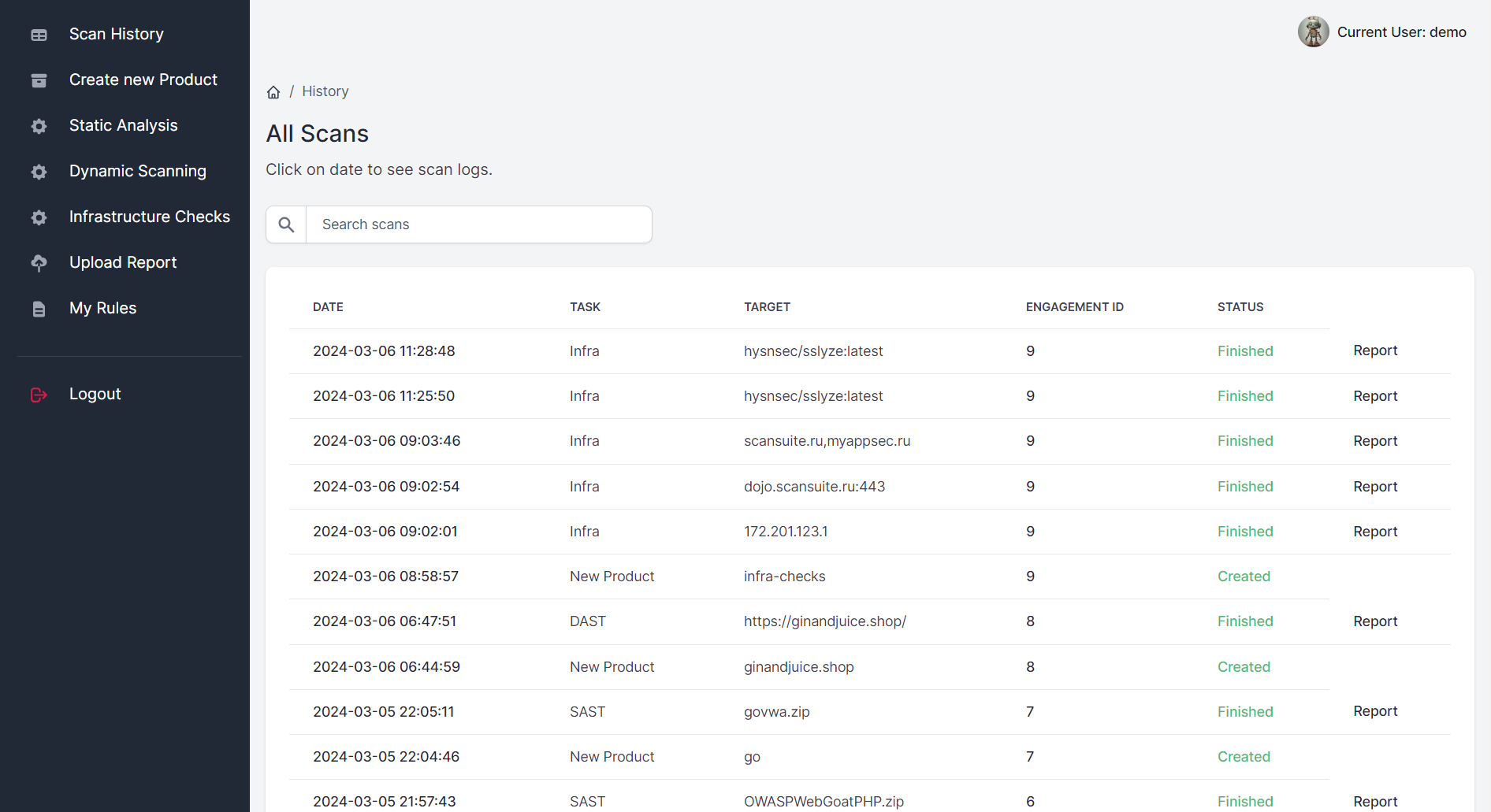
Your Complete Vulnerability Management Solution
Vulnerability scanning orchestration platform for confidential and comprehensive vulnerability management.
External Attack Surface Management
Enumeration of subdomains, hosts, websites, emails and leaked credentials
Fully automated OSINT for external attack surface mapping.
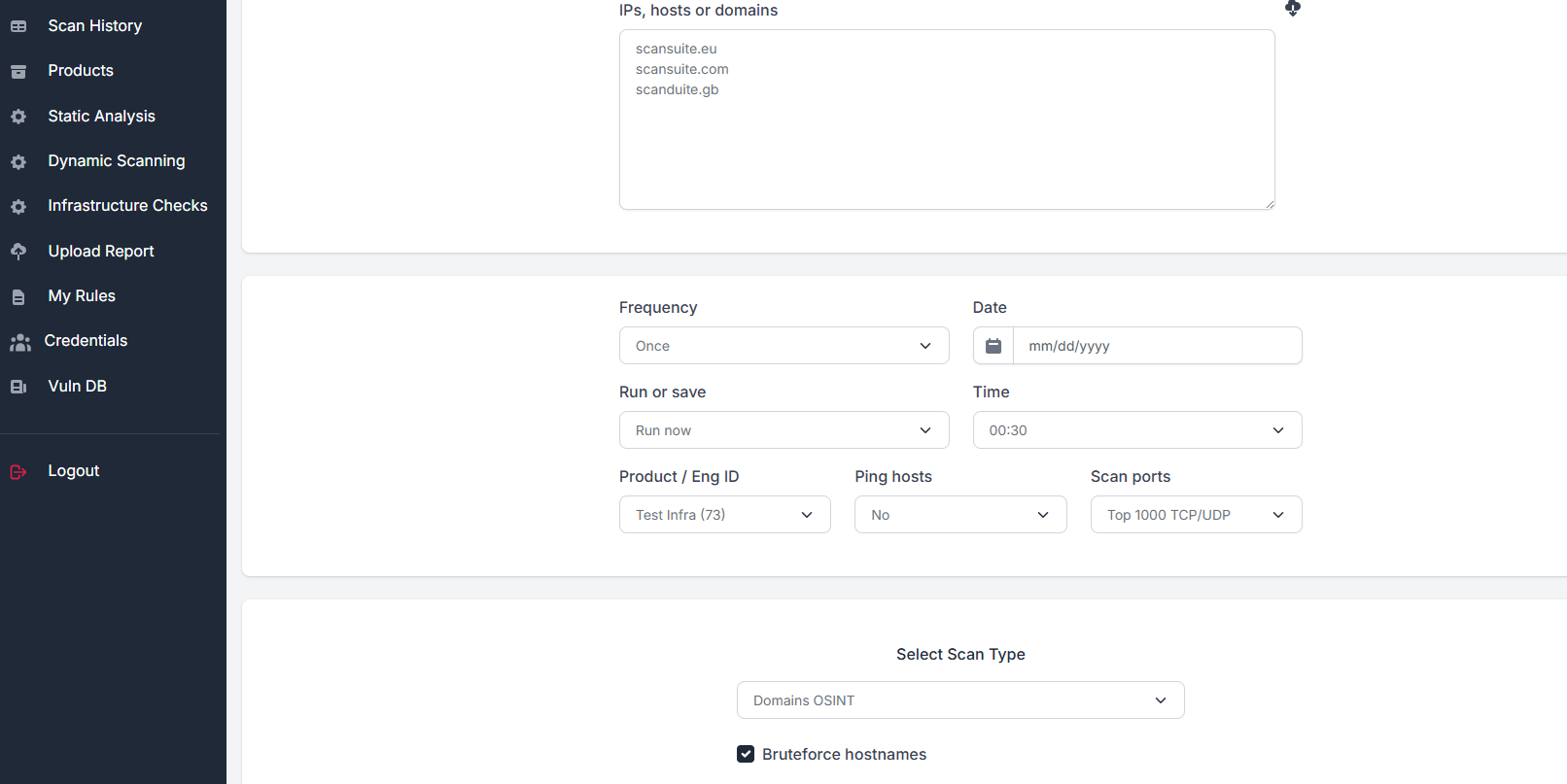
Infrastructure Checks
Vulnerability Scanning, Credentials Bruteforce, Authenticated Patching Checks, Docker Image Scans
Analyse both external and internal perimeters for active hosts, open ports, vulnerable serivces. Run bruteforcing attacks using leaked credentials and powerful wordlists. Ensure the servers patching level is up to date. Schedule scans. Analyse docker images for environmental vulnerabilities.
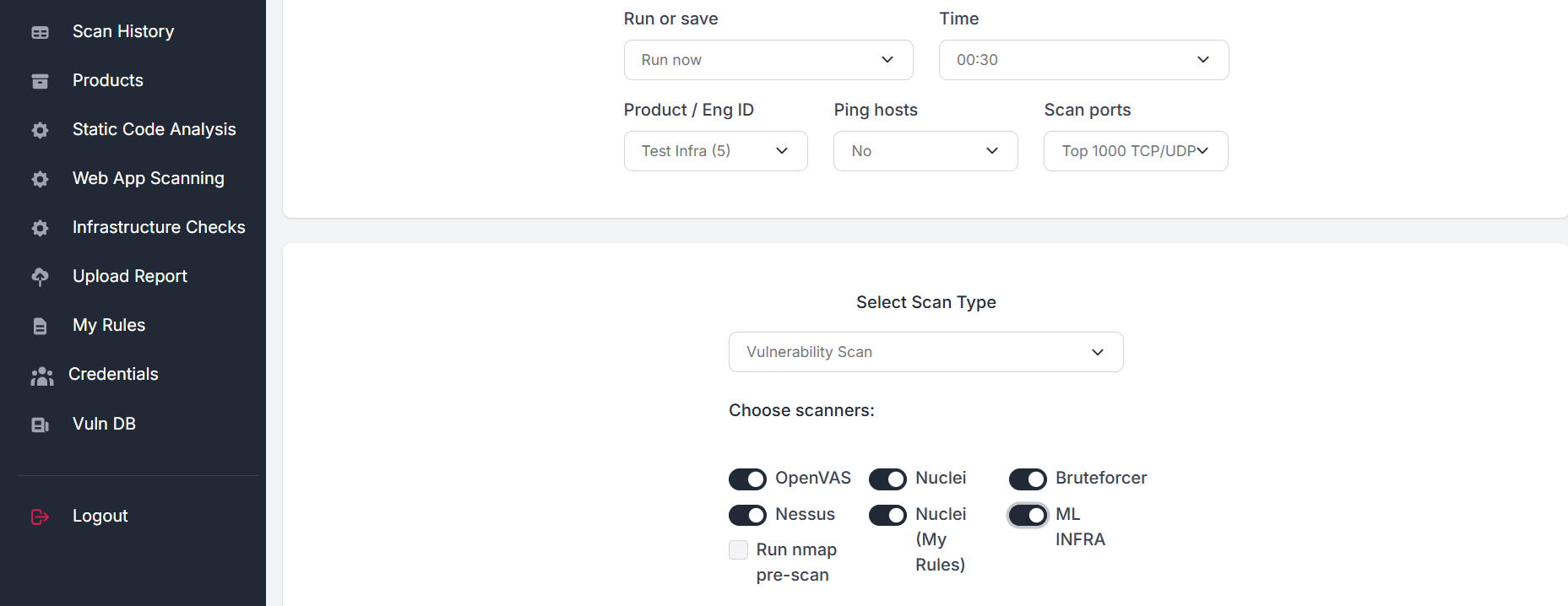
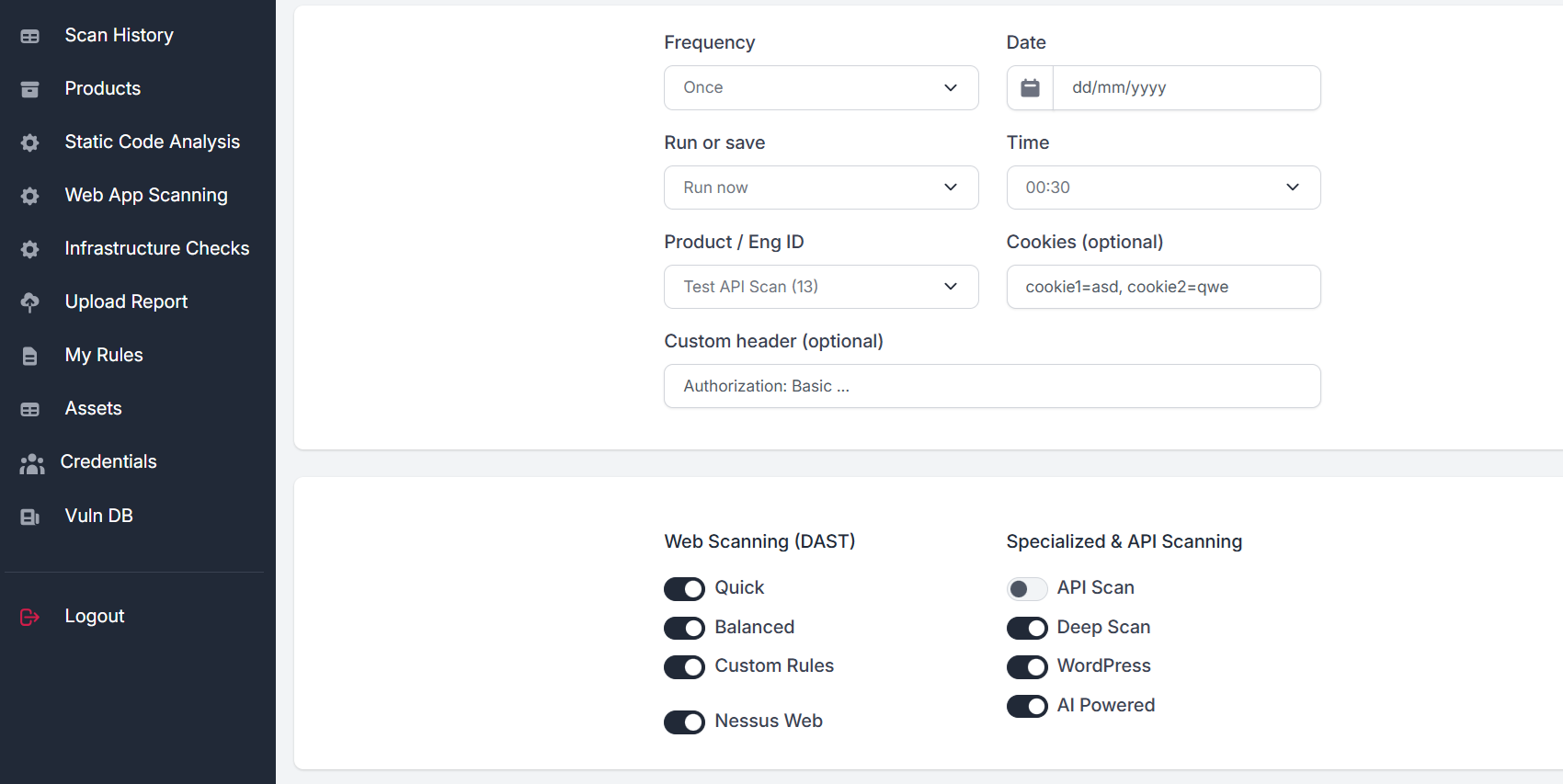
Web / API Scanning
DAST, Fuzzing, API Scans, Hidden paths, CMS analysis
Scan running web applications for known vulnerabilities and 0-days. Run authenticated scans. Schedule scans for periodic analysis.
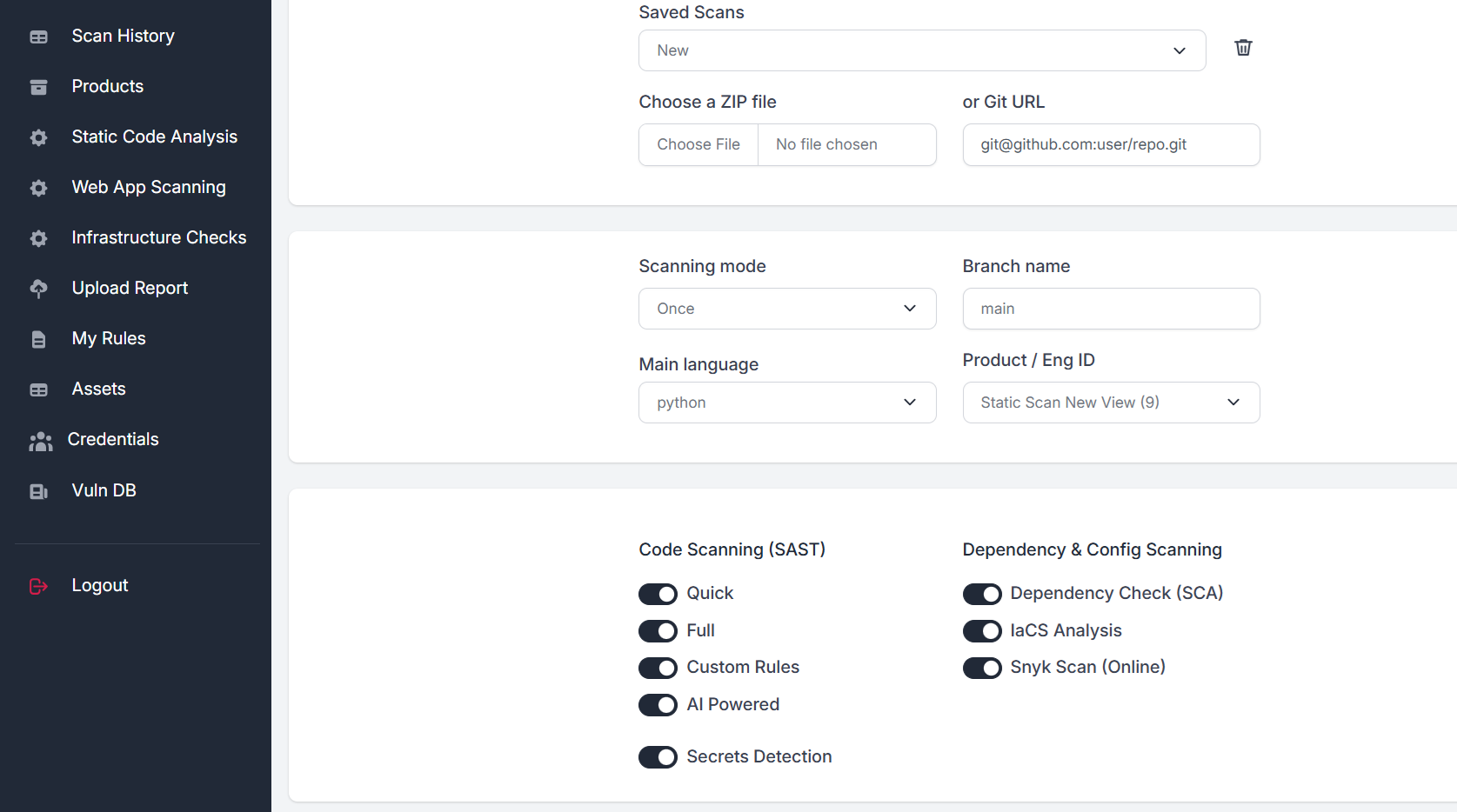
Static Analysis
SAST, ML-SAST, SCA/OAST, IACS
Find vulnerabilities in source code, dependencies and configurations. Perform incremental code analysis, schedule periodic scans. Analyse code with local and cloud LLMs.
Custom Rules
For Static, Web and Infrastructure Scanning
Scan with custom rules across all targets. Generate rules with AI.
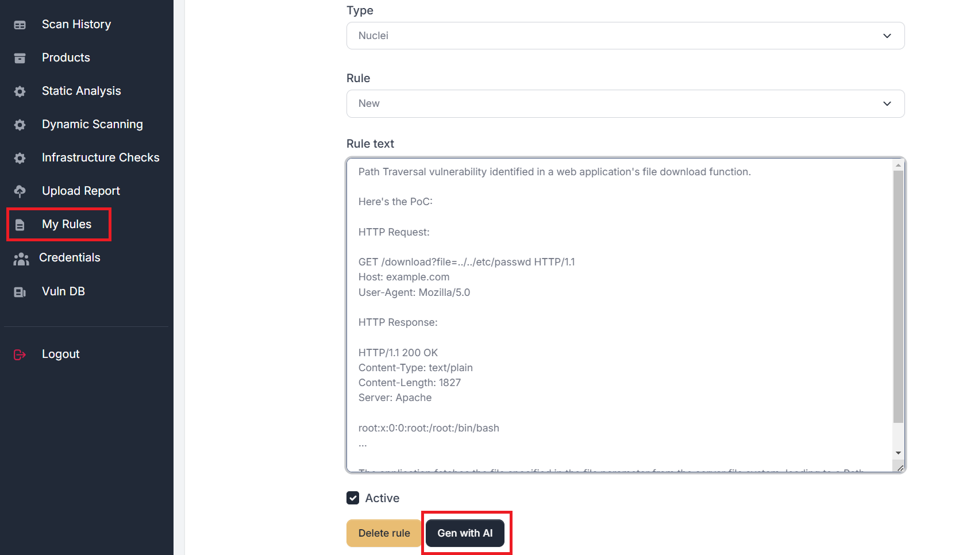
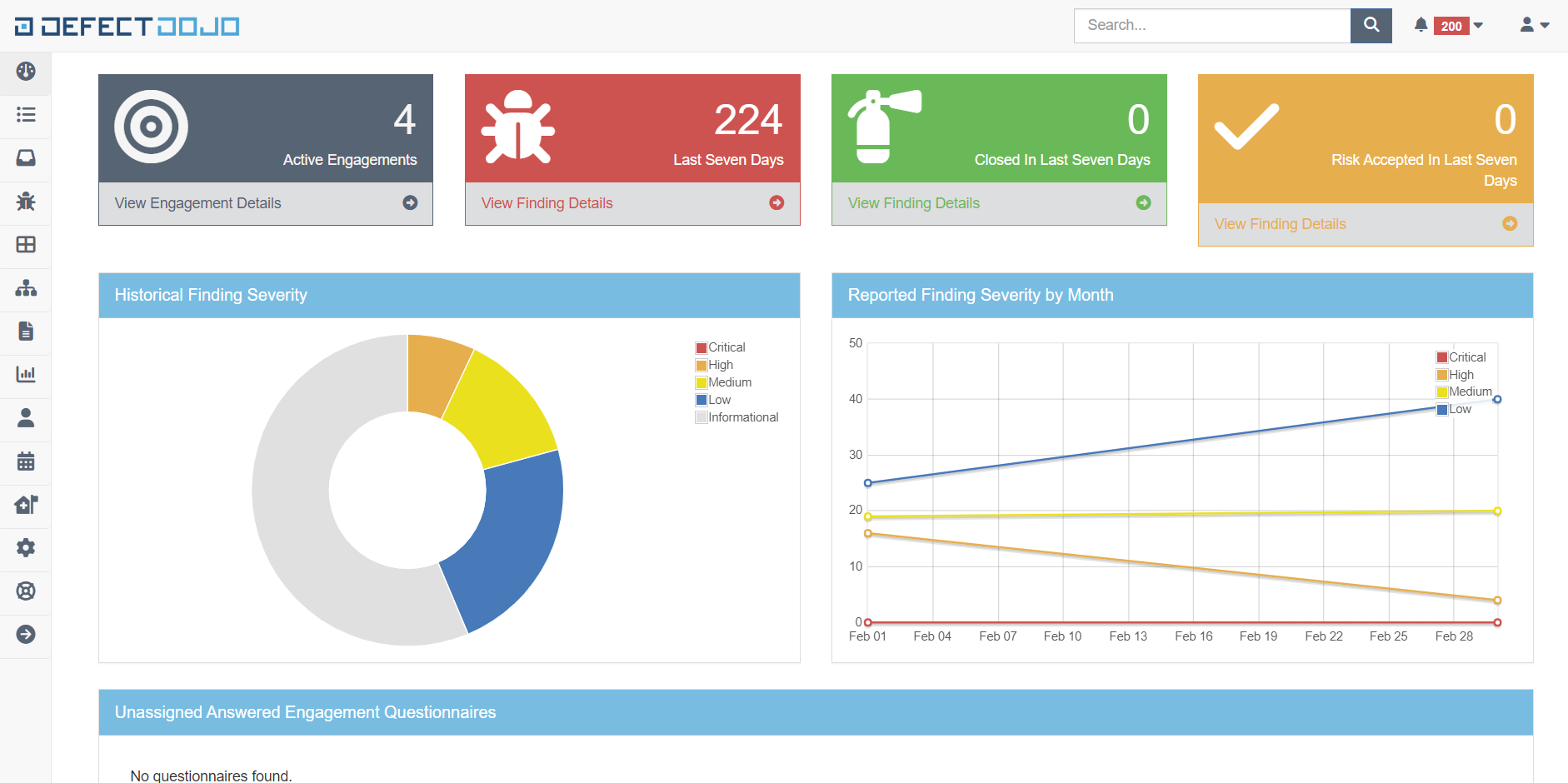
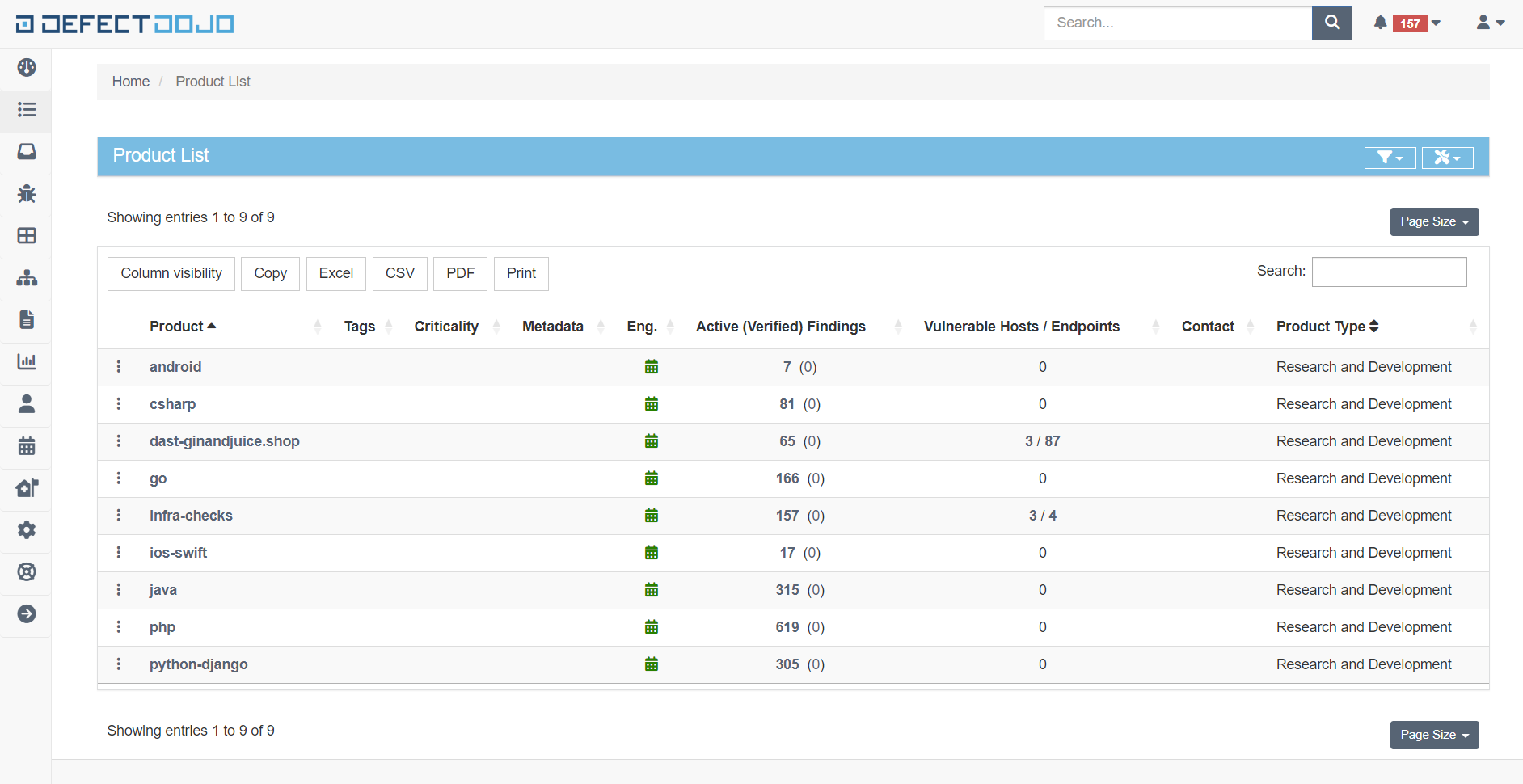
Integration with DefectDojo
Vulnerability Management System
View, track and remediate vulnerabilities. Create HTML/PDF/CSV reports. Process false positives and risk acceptance. Enable metrics, dashboards, benchmarks, SLA. Upload findings to Jira and track remediation progress.
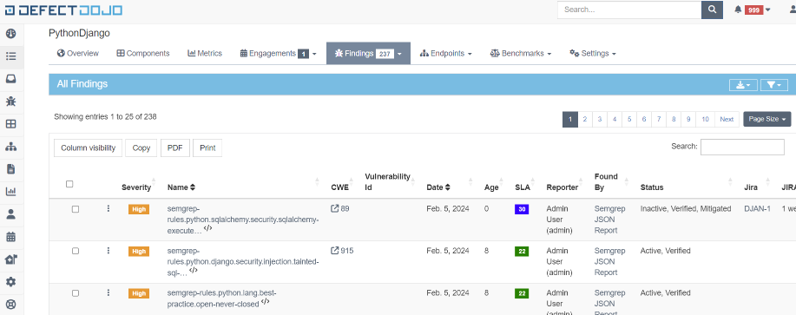
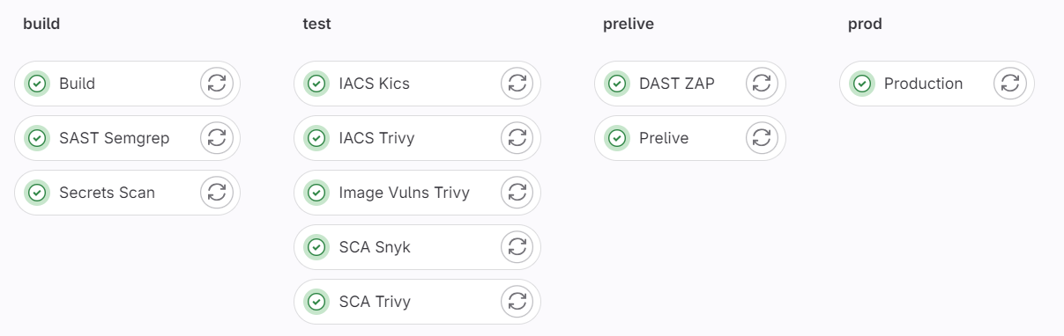
CI/CD Support
Seemless integration with CI/CD products
Run security scans within your pipelines. Analyse results in Defect Dojo.
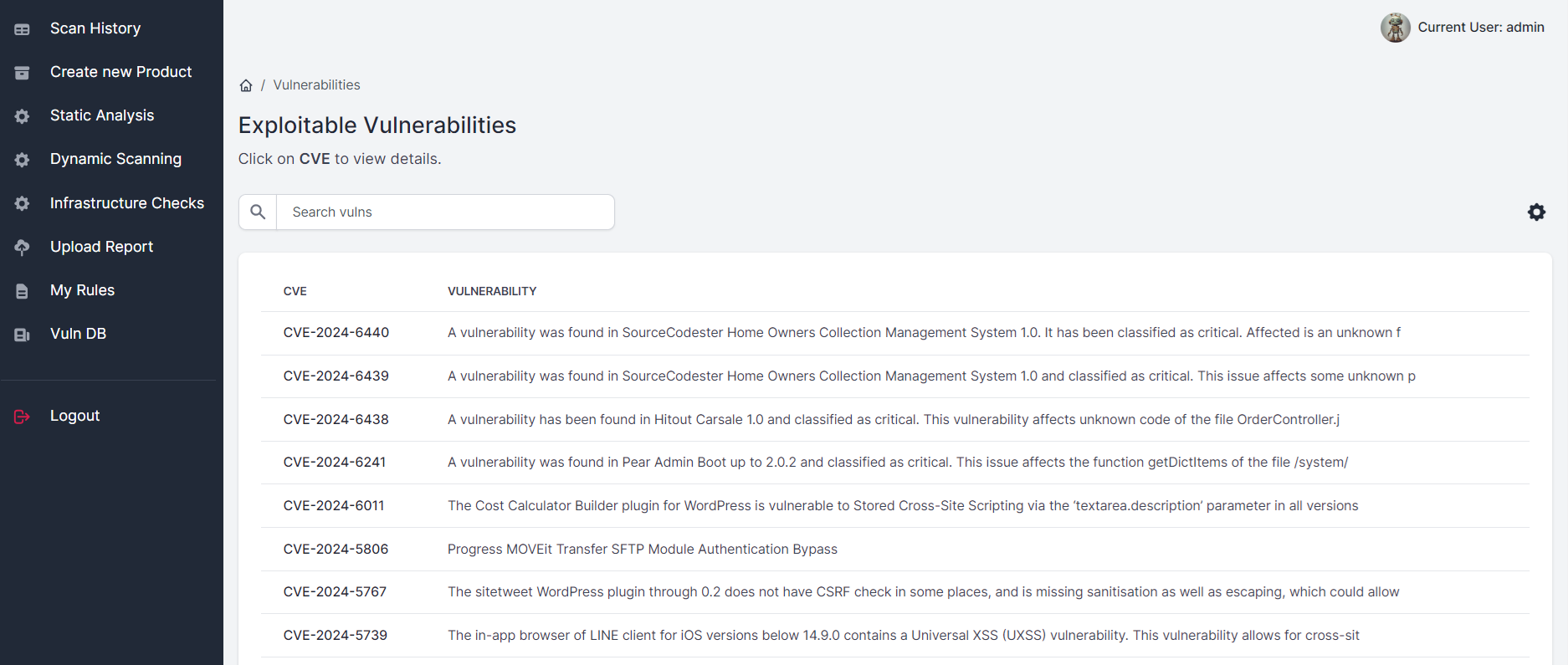
Exploitable Vulnerabilities Database
Having public exploits or noticed in malware campaigns.
The most complete database with known exploitable vulnerabilities. Auto checks during infrastructure and dependency scans.
Source Code Documentation
Automated AI generation for code repositories
Generate the source code documentation with AI. Store and read it via convenient web interface.
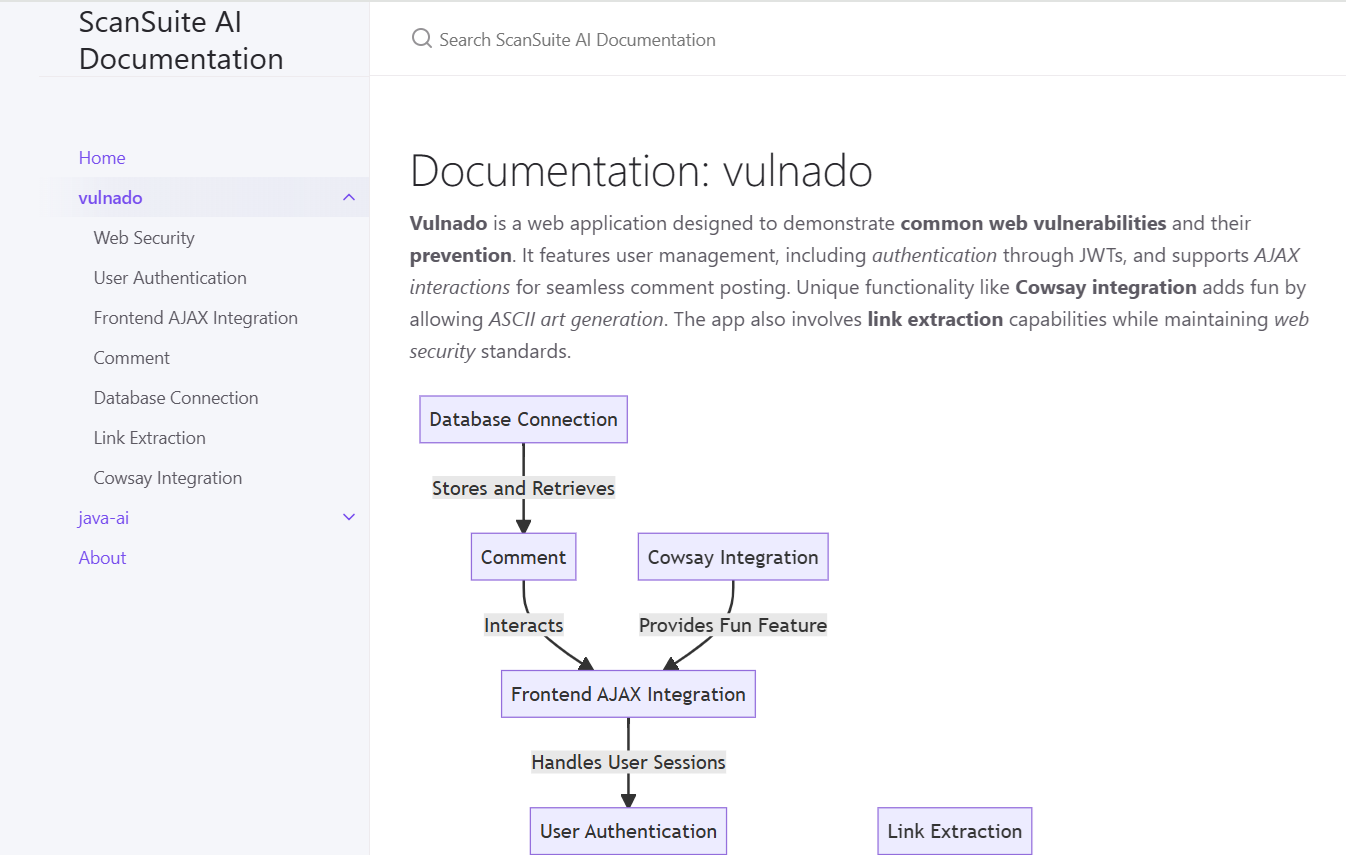
Simple and functional interface
Manage complete scanning infrastructure under single console
Main Features
ScanSuite glues the best tools together enabling comprehensive vulnerability management on-premise or in the cloud.
30+
Best vulnerability scanners enabled
20+
Development languages supported
Static Analysis
Code, Dependencies, Secrets, Infra as Code
On-premise
Manage vulnerabilities locally or in secure cloud
CI/CD
Module to support continuous security
AI
Code analysis and rules generation with LLMs
Parallel Scanning
Executed on thousands of services and codebases
Authenticated
Infrastructure and Web scans also supported
Own Rules
For custom Static, Web and Infrastrucutre scans
OSINT
Map your attack surface before hackers do
Docker Images
Vulnerability scanning and remediation
Defect Dojo
Feature rich vulnerability management
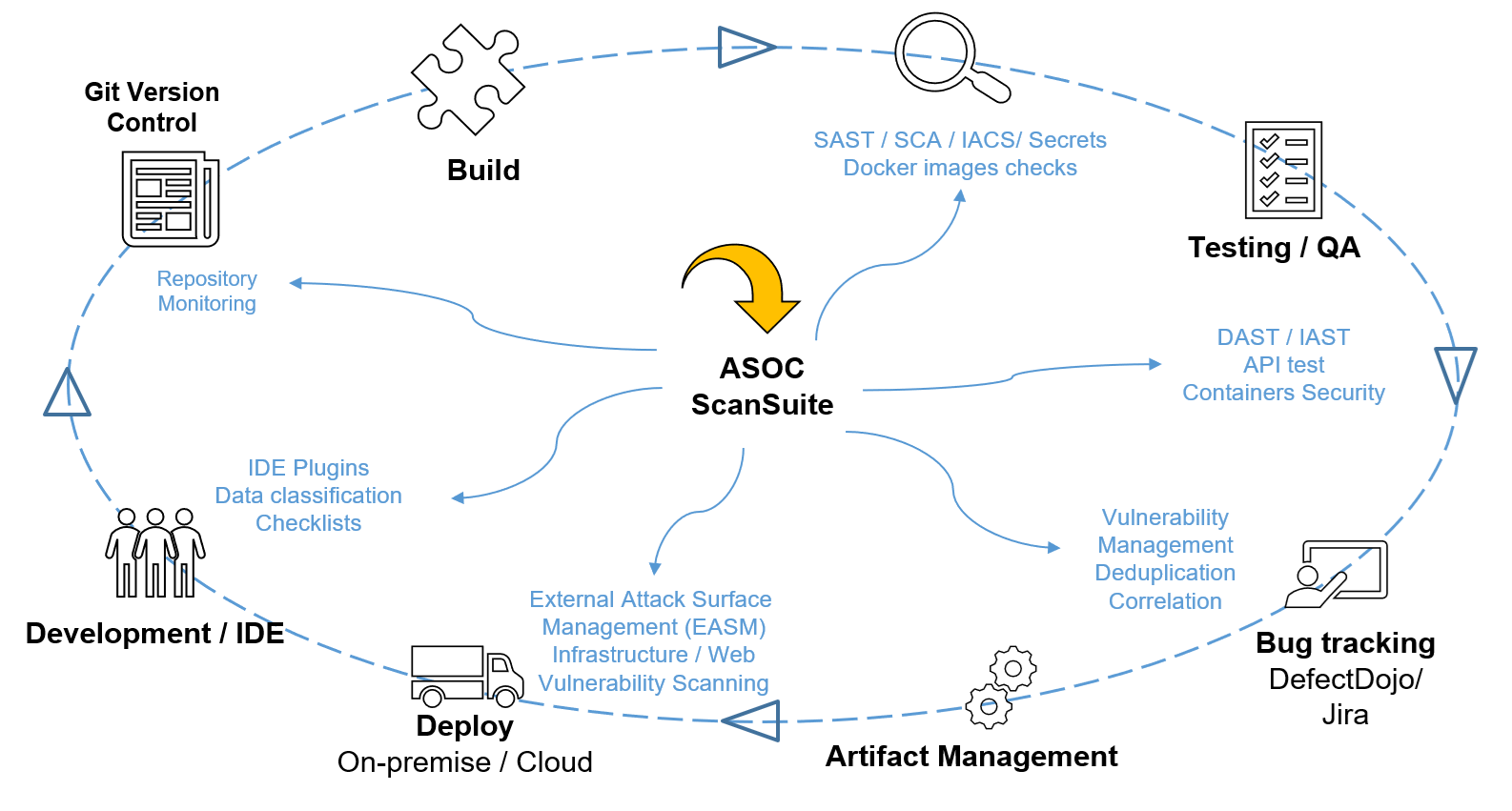
Application Security Orchestration & Correlation
Request a Demo
Contact us via info@sec-sol.ru to get a copy of ScanSuite platform.